In our latest Cyber Insurance Academy masterclass, we were joined by Martin Brea, Co-founder of DarkData, as he shared a rare behind-the-scenes look at how today’s top ransomware gangs operate and what these operations mean for businesses and insurers alike.
Are you a Premium Member? Catch up with the full recording now: Negotiating with Hackers: Ransomware & the Cyber Policy
Ransomware Gangs are Now Professional Enterprises
The industrialization of ransomware gangs has fundamentally changed how cyber risk is managed and the ransomware response. Groups today operate more like structured criminal enterprises with PR departments, affiliate recruitment programs, and public leak platforms. This shift means that a ransomware attack today is a multi-front crisis involving brand damage, legal exposure, client relationships, and regulatory risk.
The Four Main Groups in the Ransomware Threat Landscape
Martin broke down four of the most active and dangerous ransomware gangs in 2024 and 2025: RansomHub, Akira, Medusa, and Cl0p. Let’s dive into how each of these groups approaches extortion.
RansomHub
Emerging in early 2024, RansomHub is currently one of the fastest-growing ransomware gangs.
It primarily targets workstations and virtual machines, aiming to disrupt business operations and force ransom payments. Its victims are often in the technology and public sectors, and incident responders have seen its attack volume double from year to year.
RansomHub is becoming a frequent presence in 2025 breach cases and has adopted many of the tactics common to larger, more established groups.
Akira
First seen in 2023, Akira is known for its sophisticated operations and its use of access brokers. Rather than harvesting credentials themselves, Akira buys them from third parties, allowing for faster and more targeted intrusions.
However, Akira doesn’t stop at ransom notes. Their Tor-based leak site is well-designed and includes areas for browsing stolen files, viewing ransom demands, and even applying to become an affiliate. Akira is a prime example of how ransomware gangs have matured into commercialized, scalable operations.
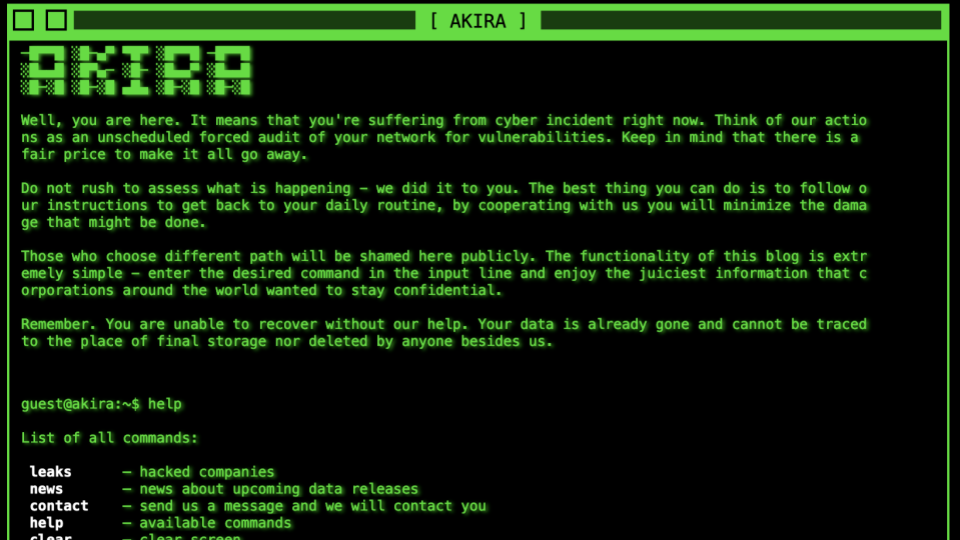
Akira’s site – hosted on the onion network -features a surprisingly polished, website-like interface. It includes sections for browsing leaks, viewing news updates, contacting the group, or requesting “help” (which essentially means paying the ransom). There’s even an option to apply to become an affiliate, highlighting Akira’s use of the ransomware-as-a-service (RaaS) model. This panel is a powerful reminder of how professionalized and commercialized cybercrime has become.
Medusa
Medusa is another highly professional group that matches Akira in scale and complexity. Active throughout 2024 and 2025, Medusa specializes in exploiting remote desktop and firewall vulnerabilities. What sets them apart is their aggressive, multilingual extortion tactics: voice messages sent via WhatsApp or Teams, often in the victim’s native language.
In one case involving a private hospital, the group directly contacted the hospital’s clients, escalating the pressure and intensifying reputational risk. This PR department-style approach is unique and adds a new layer of risk for victims and their insurers.
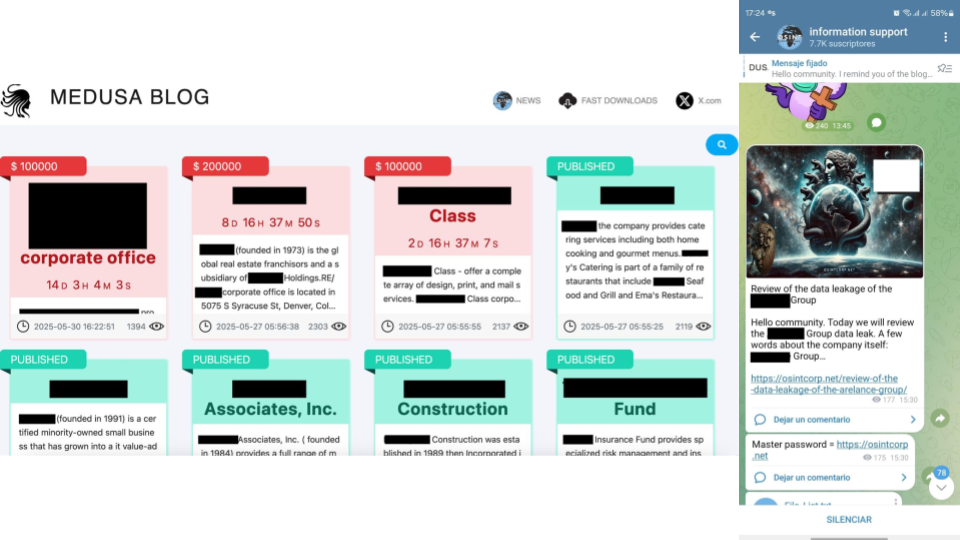
On the left, you can see their onion site, where they list victims by name and display partial company data along with the ransom demand (in USD, though payment is expected in Bitcoin). A live countdown timer signals when stolen data will be made publicly accessible, adding pressure for payment.
What sets Medusa apart is its professionalized approach to extortion. Beyond its dark web presence, Medusa also ran a public-facing “PR” operation via a Telegram channel named Oint, which mirrored updates from the leak site and broadcasted new victims daily. While that channel has since been taken down, it highlights how modern ransomware gangs are evolving to operate with the sophistication of a media outlet, extending their reach beyond the dark web to maximize reputational damage and coercion.
Cl0p
Cl0p is a well-known ransomware group that experienced peak activity in 2023, dropped off in 2024, and returned in full force in 2025. While not as consistently active or sophisticated as Akira or Medusa, Cl0p is still responsible for millions in damages and is one of the most encountered groups this year.
What makes Cl0p notable is its unusual operational pattern. Unlike other gangs that steadily grow until dismantled, Cl0p appears to cycle in and out of activity, likely due to its internal team members switching affiliations based on profitability. Their leak site, hosted on the dark web, contains ransom details, victim data, and options for joining the affiliate program.
Read More about Cl0p and it’s highly successful exploitation of MOVEit.
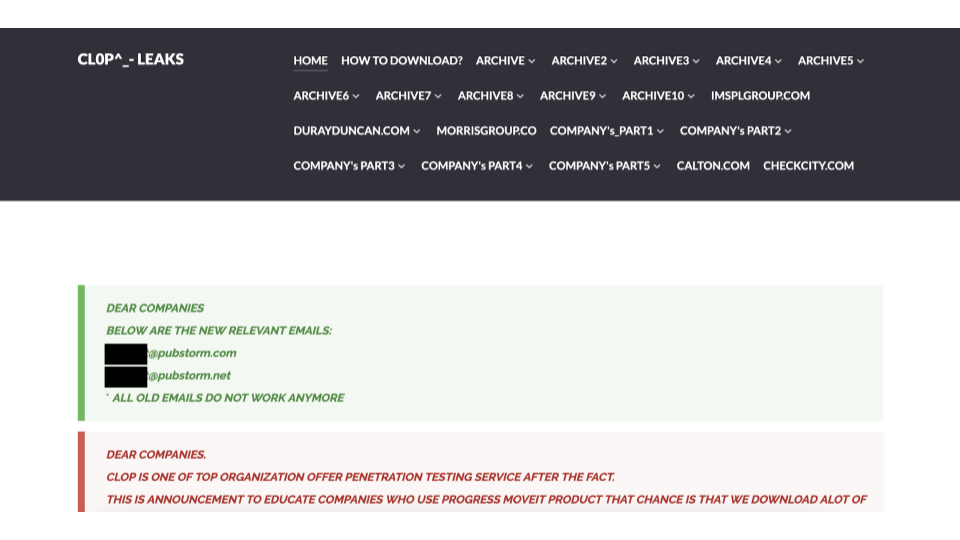
Like other ransomware groups, Clop includes clear points of contact and detailed information in the site’s header, ranging from victim lists to malware details and even instructions on how to become an affiliate.
What’s particularly striking here is the ease with which individuals can connect with or even join these criminal operations. The accessibility and structure of these sites reveal just how organized and commercialized ransomware has become, which contributes to millions in global losses.
To learn more, watch the full recording now! Available online for premium members.
From a cyber insurance perspective, this new evolution in the ransomware threat landscape is very concerning. The ease of joining affiliate programs, the adoption of multilingual extortion techniques, and the use of aggressive public pressure tactics mean that underwriters must assess not only technical exposure but also an organization’s preparedness for high-pressure extortion scenarios.





