Our most recent masterclass, Beyond the Policy: Managing Cyber Claims with Technical Incident Response in collaboration with Arctic Wolf, covered the incident response process. A cyber incident can trigger significant financial and operational disruption—but with the right incident response (IR) coordination and cyber insurance strategy, you can help policyholders recover faster and minimize losses.
What is the Incident Response Process?
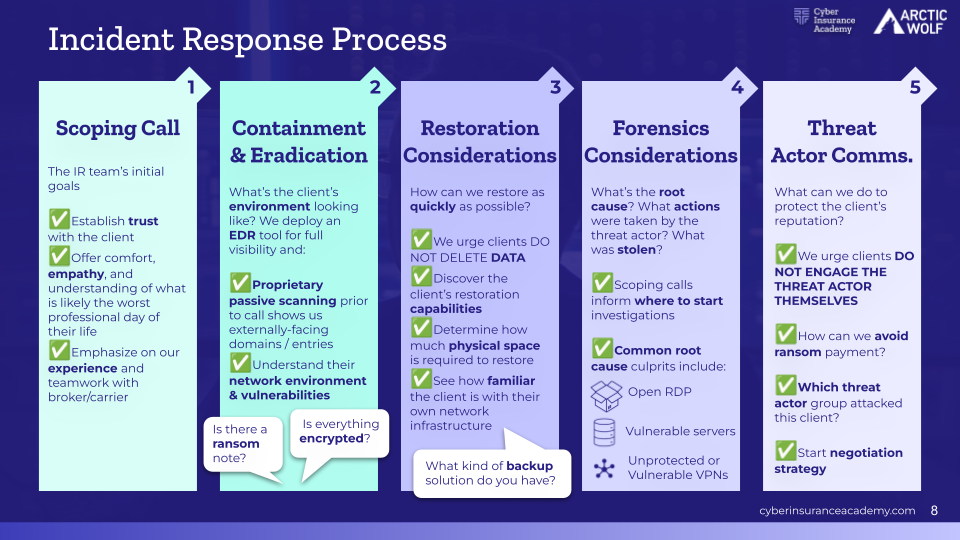
When a cyber incident occurs, a structured and strategic incident response process is critical to minimize damage, contain the threat, and support recovery. The incident response process typically follows five key steps—Scoping Call, Containment & Eradication, Restoration Considerations, Forensics Considerations, and Threat Actor Communications. Each step plays a vital role in helping organizations navigate the chaos of a cyberattack, restore operations, and make informed decisions.
1. Scoping Call
The scoping call marks the beginning of the incident response process and plays a crucial role in establishing trust between the client and the response team. This initial conversation is focused on setting clear expectations, providing immediate guidance, and reassuring the client. During the call, the incident response (IR) firm shares recommendations and outlines the next steps, emphasizing their experience in handling similar situations. This early alignment helps the client feel supported and confident in the team’s ability to manage the crisis effectively.
2. Containment & Eradication
This phase of the incident response process is centered on securing the environment and ensuring that the threat actor is no longer active within the network. Tools such as Endpoint Detection and Response (EDR) are deployed to monitor and neutralize malicious activity, while other cybersecurity measures are implemented to prevent further encryption, data exfiltration, or surveillance by the attacker. The goal is to swiftly and thoroughly remove the threat actor while preserving the integrity of the systems and data for future forensic review.
3. Restoration Considerations
The third phase of the incident response process involves assessing backup strategies and developing a tailored plan to bring systems safely back online. While clients are often eager to restore operations as quickly as possible, restoration must be approached thoughtfully. One of the key recommendations is to avoid deleting or rolling back any data until after consulting with the IR or restoration vendor, as this could compromise valuable forensic evidence or unintentionally remove critical files. Restoration plans vary depending on the client’s internal capabilities—larger organizations may handle the process internally, while smaller businesses may require more hands-on support.
4. Forensics Considerations
Forensic analysis is a pivotal component of the incident response process, focused on uncovering how the threat actor gained access to the environment and whether they established any persistence mechanisms for future intrusions. This investigation seeks to identify and eliminate these vulnerabilities to prevent re-entry. Additionally, the forensic team works to determine what data was accessed or stolen. These insights are critical for informing legal, regulatory, and business continuity decisions.
5. Threat Actor Communications
Communicating with the threat actor—especially during a ransomware event—is a delicate and high-stakes process. Clients are strongly advised not to engage with attackers directly. Instead, firms like Arctic Wolf provide specialized threat actor negotiation teams that handle these communications on behalf of the client. These experts understand the behaviors, demands, and negotiation tactics of various threat groups and aim to minimize harm. Whether the goal is to avoid paying a ransom altogether or to negotiate a lower amount, the process is carefully coordinated with the client, legal counsel, and insurance carrier to ensure alignment and informed decision-making throughout the negotiation.
To delve deeper into managing cyber claims and incident response, a full recording of the masterclass is available!





