Stu Panensky is a Founding Partner at Pierson Ferdinand, specializing in cyber risk privacy and data security. He has extensive experience in teaching cyber insurance professionals about regulatory issues, cyber claims handling, and cyber litigation trends. Following his highly popular Masterclass on Digital Supply Chain Cyber Risks, Stu shares his insights and best practices on handling third and fourth-party cyber risks.
All organizations face cybersecurity and data privacy risks associated with third-party vendors and other business partners in their digital supply chain. Some of these risks potentially involve fourth or even fifth parties that are digitally connected, but otherwise unknown to the company. When formulating the appropriate information security and data privacy policies, businesses must consider and employ best practices for mitigating risks from both upstream and downstream digital connectivity.
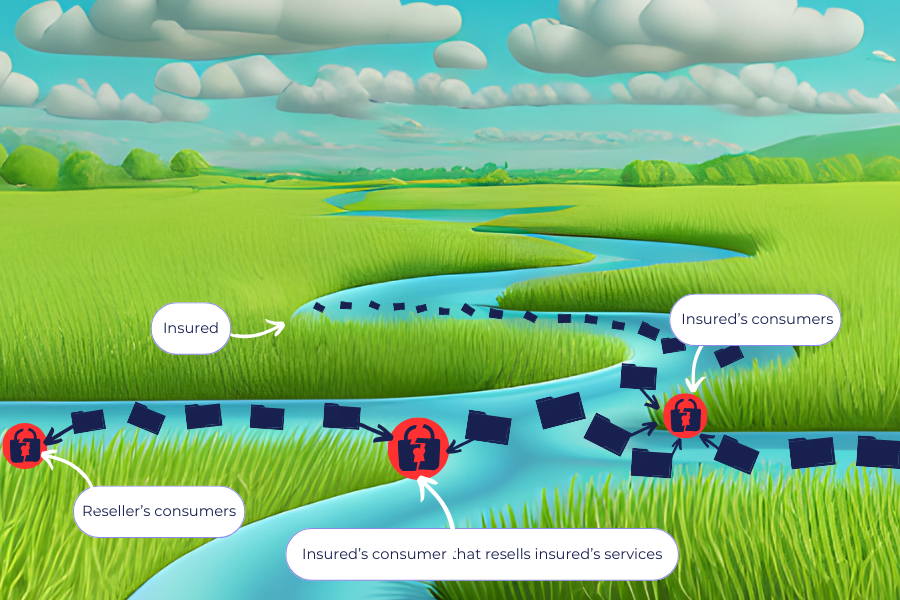
Visualizing Upstream and Downstream Cyber Risks
Imagine all digital connectivity as river waters. Your policyholder sits somewhere in the middle of the river connected to other entities both upstream and downstream.

Your policyholders ’distributors, retailers or even consumers sit downstream. The digital assets – (the systems and data) flow from the policyholder to its downstream consumers. Upstream from the policyholder sits the vendors and suppliers that your policyholder relies on for its digital operations. Sometimes this includes the processing of sensitive electronic data. This article explores the risks posed by this connectivity.
Upstream Third-Party Cyber Risks
Businesses routinely entrust sensitive data, like employee or customer personally identifiable information, financial information, and corporate trade secrets to third-party vendors, suppliers, and business partners. A security breach or privacy incident at any of these entities potentially affects this sensitive data. This exposes the organization to risk including financial loss, compelled legal compliance and reputational damage relating to what is essentially someone else’s breach.
Upstream cyber risk refers to the potential for a security breach or privacy incident at a third-party vendor, supplier, or business partner to expose a policyholder’s sensitive data.

Let’s consider the mountain river scenario. Weak security practices of a policyholder’s vendors are like polluted tributaries. These polluted streams can introduce contaminated or compromised data into your policyholder’s system, even if their own security is strong.
To mitigate these upstream risks, we advise companies to perform a risk assessment of vendors’ security practices as part of their overall governance, risk management and compliance (GRC) programs. This includes evaluating vendors’ security and data privacy controls, policies, and procedures for the collection and use of the data at issue. Companies can monitor their own vendor privacy policies and data security agreements ensuring clear data protection obligations are understood and accepted by all parties.
Negotiating Security and Data Privacy Terms
Contractual agreements with third parties should clearly define expectations regarding cyber security and data privacy. We advise our clients to address these issues upfront as part of the bargaining process. Key provisions include:
- Data Security Standards: These outline the vendor’s obligations to safeguard sensitive data, encompassing security controls, breach notification procedures, and liability for data breaches and attending legal and regulatory obligations.
- Privacy Policies: These define how the vendor collects, uses, and shares sensitive data, ensuring transparency and alignment with the policyholder’s own privacy practices.
- Audit Rights: A reservation of the right to audit vendor security practices to ensure ongoing compliance. What is inspected is expected.
- Indemnification: Vendors should indemnify companies for any damages arising from security incidents.
- Cyber Insurance: Vendors should maintain adequate cyber and other insurance limits to offset any potential liabilities. We advise our clients to keep a record of the cyber insurer and the limit for each vendor. Also consider requiring fidelity or commercial crime insurance.
- Limitation of Liability: While vendors may seek limitations on liability, organizations should carefully negotiate these terms to manage risk exposure.
Monitoring Third-Party Compliance
Obtaining commitments from upstream third parties is important. Regularly monitoring performance and compliance to ensure vendors adhere to security and data privacy standards is equally important in a company’s security program. This can involve:
- Security Audits: Regular audits by qualified third parties assessing the effectiveness of the vendor’s security program.
- Vendor Reports: Reviewing vendor-provided security reports helps identify potential gaps in their security posture.
- Vendor System Access: In some cases, organizations may request access to vendor systems for independent security assessments.
- Media Monitoring: Staying informed of any security incidents involving the vendor helps identify potential risks.
- Communication: Regular communication with vendors regarding security practices strengthens the relationship and fosters a culture of security awareness.
Downstream Third-Party Cyber Risks
Sensitive data can also be exposed through vulnerabilities in downstream third parties, such as distributors, retailers, and consumers. If these entities are hacked, the organization’s own data may be compromised.
Downstream cyber risk arises from vulnerabilities present in a policyholder’s distribution channels, retailers, or even consumers. These entities, further down the supply chain, can be compromised, potentially exposing the policyholder’s own sensitive data that resides within their systems.