The Cyber Insurance Academy was delighted to host Keely Wilkins and Andy Igel, both from Check Point, in a recent Email Security Masterclass. Topics covered included key trends relating to email security & BEC attacks, the impact of ChatGPT on email security (a summary of which can be found here), best practices for insureds should follow to mitigate the impact of attacks via emails and helpful metrics that can be applied to calculate the efficiency of insureds’ email security vendors. With cyber brokers, in particular, taking on a more interactive role with their clients and experiencing a higher volume of touch points throughout the year, these Masterclass lecture notes are designed to summarize key considerations to build greater trust between insureds and the insurance professionals working with them.
Email Attacks Cost More than other Vectors
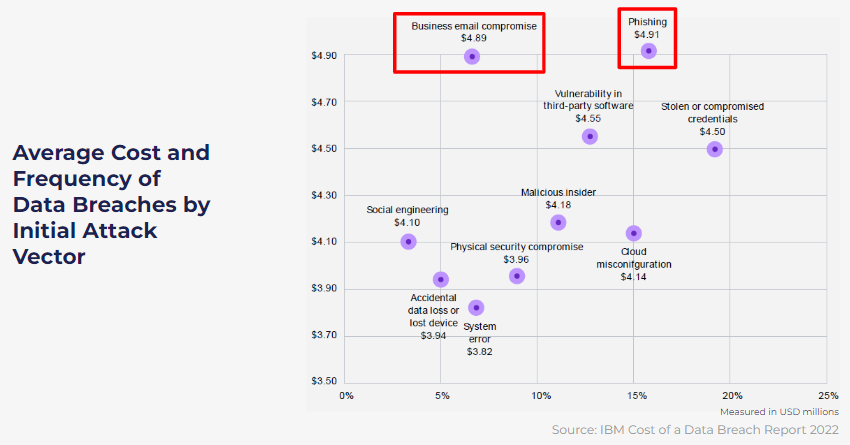
On average, a phishing breach incurs a cost of just under $5 million per breach. It is important to note that the precise financial impact varies based on factors such as the size of the organization and the scale of the breach. According to IBM’s findings, these types of breaches occur approximately 16% to 17% of the time. Similarly, business email compromise yields slightly lower costs, averaging around $4.89 million per breach, and transpires around 6% to 7% of the time.
Compromised Credentials are critical factors in both phishing and BEC. This entails the reuse of email addresses and usernames across various accounts. This interconnected web of reused credentials allows threat actors to perpetuate their attacks until they strike the jackpot. IBM’s data highlights the significant role played by social engineering, with an average cost of $4.1 million per event and occurring at a frequency of approximately 3% to 4%. It becomes evident that these elements are intertwined and cannot be viewed in isolation. The exploitation of compromised credentials through social engineering techniques serves as a linchpin for successful phishing campaigns.
It is important to mention that the chart does not touch upon ransomware, as it pertains more to the payload of an attack rather than the attack vector itself. Ransomware can be delivered as a consequence of a phishing attack, acting as the harmful payload. While this specific topic was beyond the scope of Check Point’s Masterclass, it underscores the multifaceted nature of cyber threats and the interconnectedness of various attack vectors and payloads.
Email Security Best Practices & Mitigation Techniques
Given the high cost associated with email security attacks, it is imperative for insurance professionals to have a comprehensive understanding of the various techniques employed by malicious actors, helping their clients to mitigate the potential financial and reputational impact and, in so doing, tightening their relationships.
Staff Training
One crucial aspect of any cybersecurity strategy or action plan is staff training. By providing comprehensive cybersecurity awareness training, employees can learn to recognize and avoid phishing attempts, business email compromise, and the influence of social engineering techniques. This training empowers individuals to make informed decisions and significantly reduces the risk of costly breaches, ensuring the protection of sensitive data.
The Right Security Professionals in the Right Roles
Whether they are in-house or contracted from a managed security service provider (MSSP), these professionals play a paramount role in implementing, configuring, monitoring, and taking action on the necessary security measures. While organizations with limited resources may opt for an MSSP to handle their security needs, larger organizations that have the means and expertise may choose an in-house security team. However, regardless of the approach, clear objectives and escalation procedures must be established and understood by all parties involved, including the MSSP, who should also carry their own cyber insurance.
Prevention-First Security
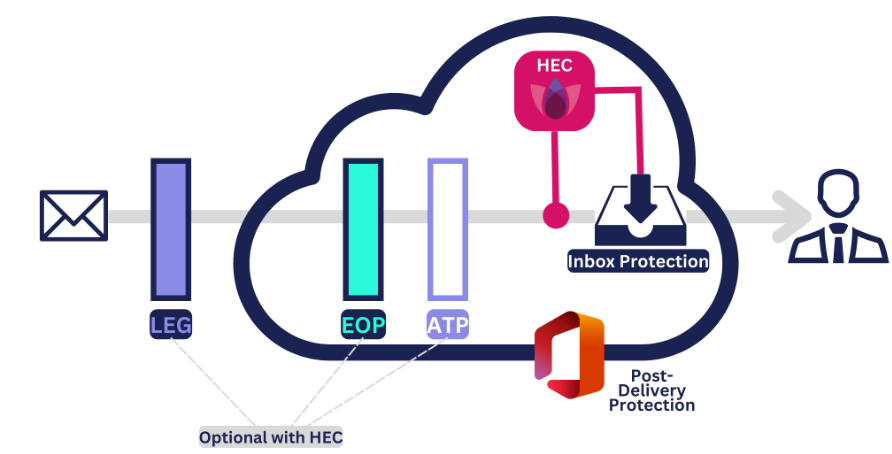
Cloud-based email services, such as those offered by Google and Microsoft, come with built-in security features, which are generally effective. However, on top of this, there are two main methods for securing email that are commonly found in today’s market. The first is through Legacy Email Gateways, also known as Secure Email Gateways, which were designed for on-premises email servers but may not be as effective against newer threats since they require heavy configuration. The second method is API email security, which directly integrates with the cloud provider’s system using AI and machine learning for better threat detection. However, API solutions are more reactive rather than preventive, as they focus on post-delivery protection.
A proactive prevention approach, like the one offered by Check Point’s email security solution, called Harmony Email Collaboration (or, HEC), can block threats before they reach the user’s mailbox. This is where Keely and Andy distinguished Check Point’s capabilities from other email security solution vendors.
Choosing The Right Email Security Vendor: How To Assess Your Insureds
We have compiled four key words from Check Point’s Masterclass. Make sure you understand them and then tune in to the recording to see these terms in action.
Catch rate:
A catch rate serves as a measure of effectiveness for security solutions, with various testing labs assessing their efficacy, similar to organizations like Consumer Reports. When a solution boasts a 95% catch rate, it indicates that it successfully prevented or intercepted 95% of the attacks it encountered. However, there remains a gap in research regarding the financial implications of the remaining 5% of risk assumed by consumers or insured individuals.
Listen to Keely explaining catch-rates and the cost of remaining risk here:
Quarantine
When something is prevented, it is stopped before it occurs. A robust security solution should proactively prevent malicious attacks rather than merely reacting to them. This is particularly important, for instance, given the alarming rise of zero-click attacks, where the user doesn’t even need to take action for the attack to take effect. An effective solution should intercept and neutralize such threats before they reach the user’s mailbox. Additionally, prevention includes the crucial practice of quarantining, akin to the measures we’ve become acquainted with during the COVID-19 pandemic, ensuring harmful elements are isolated and contained in a secure location separate from the rest. This ability to segment and protect is a fundamental feature that every security solution should possess.
Sandbox
A sandbox, in the realm of security and information technology, serves as a secure environment to store and run applications or processes without posing any risk to the overall system. It acts as a testing ground, allowing users to experiment and evaluate software safely. When it comes to security, this is where the significance of antivirus and anti-malware protection becomes evident. While antivirus software has been a household term for years, it no longer suffices in the face of evolving threats. Similarly, relying solely on a gateway approach for email security is inadequate. In today’s landscape, comprehensive security solutions encompass more than just antivirus measures. Endpoint solutions, such as EDR (Endpoint Detection and Response), integrate sandboxing capabilities alongside antivirus and advanced anti-malware features. Therefore, a robust security solution should encompass all these aspects to effectively safeguard systems and data.
Policy
In the realm of security, a policy serves as a guiding framework that outlines the actions to be taken based on predetermined criteria or adaptively as the situation demands. Essentially, a security policy directs the system on how to respond when specific conditions are encountered. It is akin to a set of instructions that dictate the appropriate course of action, ensuring that security measures align with predefined guidelines. By adhering to these policies, organizations can effectively navigate the complex landscape of security threats and mitigate risks.
In conclusion, against the escalating costs of email security attacks , insurance professionals have a crucial role in understanding their impact and being able to discuss best practices with their insureds. These include staff training, deploying the right security professionals, adopting a prevention-first security approach, selecting the appropriate email security vendor, and ensuring that email security solutions are correctly configured. By staying informed and implementing robust measures, insurance professionals can effectively safeguard their clients’ interests and strengthen their relationships in the face of evolving cyber threats.







