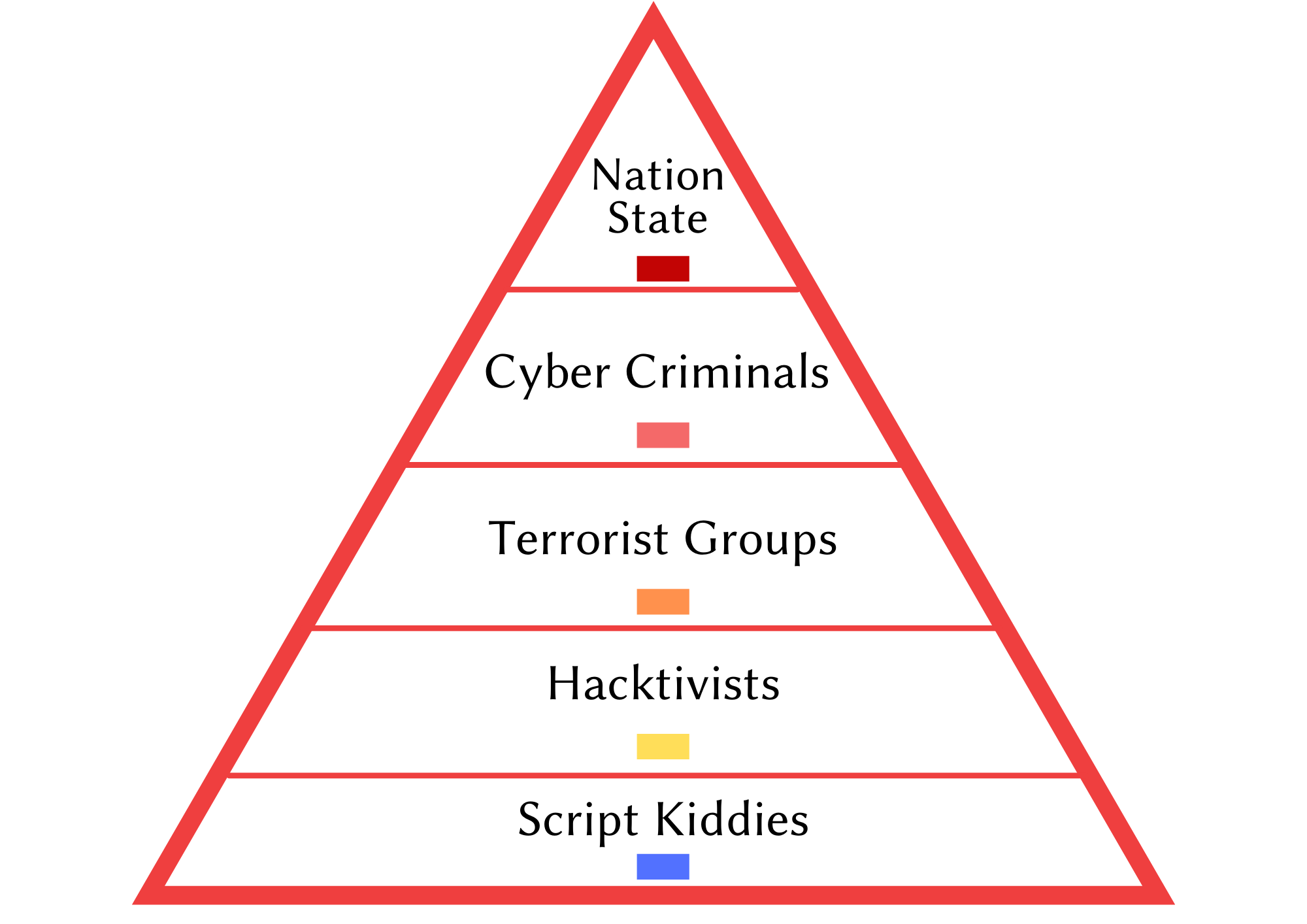
Cyber threat actors include a state, group, or individual which might maliciously intend to exploit technological and cyber security vulnerabilities in an organization to gain unauthorized access to its information systems. Threat actors are classified into different categories according to their sophistication, skill, motivations, and resources. Each class of threat actors will carry a certain level of risk, depending on the circumstances under which they present.
Why do organizations need to consider cyber threat actors as part of their risk management process?
It is best practice to adopt a threat-driven approach to effectively safeguard against the risks associated with malicious threat actors.
This methodology considers the vulnerabilities, assets, and defense mechanisms that threat actors will aim to manipulate. This, in turn, enables organizations to allocate a proportionate level of resources to defend their assets.
In other words, a threat-driven approach encourages cyber risk management in an organization to be anchored in questioning who the threat actors are, what are they interested in, and how they could go about executing their attack.
So let’s get to grips with each of these threat actors to make sure our resources to combat them are well ahead of the curve. We will look at each one in order of the risk they pose (high to low), unpicking their identity, what makes them tick, and their level of sophistication.
What Cyber Threat Actors Do Insurance Professionals Need to Know About?
1. Nation States and State Sponsors
You might have heard lots of talk in the news recently about Russian cyberattacks on western governments. Although Russia has refused to own up to anything, the US government has alleged that Russian cyberattacks manipulated the minds of the American public and interfered with the votes cast in both the 2016 and 2020 elections. For example, the Kremlin has been accused of hacking the Hilary Clinton campaign, releasing damaging propaganda, and probing voter databases for insecurities.
Russia, alongside the US, China and the UK, is considered one of the world’s superpowers in the global cyberwar. They could be considered nation-state actors.
These are government-sponsored groups that illicitly gain access to or damage the networks and information of other governments. But the impact of these threat actors is far more wide-reaching than simply stolen data or network breakdowns – nation-states have the potential to create political, social, and economic disorder through their campaigns. These threat actors will often go to extremes to cover their tracks using highly sophisticated resources, personnel, and extensive planning and coordination, making it difficult for cyber security experts to trace attacks back to them.
Motivation: Military espionage, influencing public opinion through disinformation disseminated via social media, and manipulating government decision-making processes.
2. Cyber Criminals
Organized crime gangs have long leveraged the world of cyber to line their pockets. Wanting to get rich quick, these criminals use highly sophisticated techniques to focus primarily on cash- or data-rich businesses, although individuals and home networks have been known to come under fire as well. Once armed with stolen data, they are able to sell valuable information on the black market to the highest bidder. Their weapon of choice is often ransomware which can be used to extort victims.
One of the better-known cybercriminal gangs has been REvil, short for Ransomware Evil, which appears to have mysteriously disbanded in the Summer of 2021. As the name suggests, this group’s cyberattack of choice is ransomware: the gang has raked in a fortune by threatening to publish stolen information on their own blog unless sums of money are paid to them. Gang members have targeted thousands of companies but have also been known to make a beeline at A-listers – some names you might recognize include Lady Gaga and Donald Trump.
3. Terrorist Groups
Terrorism, by definition, seeks out every means available to spread fear, unrest, and strife around the world. Harboring financial and geo-political motivations, terrorist groups today are able to leverage cyber weapons to disrupt essential services, steal valuable data, and cause damage to critical services and organizations that prevent them from achieving their terror missions. However, these groups tend to boast less sophisticated cyber attack methods.
4. Hacktivists
A playful combination of the words ‘Hack’ and ‘Activism’, hacktivism is the act of hacking for politically or socially motivated purposes. Hacktivists are often motivated to draw attention to perceived injustices or unethical conduct. They may launch an attack campaign to take revenge, challenge distasteful ideology, or cause embarrassment to individuals or organizations who they consider to have behaved poorly. On the whole, the level of resources and sophistication is low-medium.
Perhaps the most iconic example of this class of threat actors is the Anonymous group: their memorable white masks and celebrity targets have often stirred media frenzies. Lulz Security, also known as LulzSec, was a hacktivist organization which, at their peak, were responsible for the hacking of several British newspapers and the planting of fake news.
5. Script Kiddies
These are less experienced malicious hackers who use off-the-shelf software to hack. Most script kiddies are more motivated by the thrill or notoriety that they can achieve from a successful cyberattack and will never evolve into full-time hackers.
So there they are: the common threat actors which every cyber insurance professional should be aware of. Any insurer should want to see that its clients have identified their specific threat actors and the damage they are capable of creating, followed by a comprehensive security plan which answers that risk. After all, you can’t build a winning defense strategy without first anticipating your opponents’ first move.
Interested to learn more about the latest developments in cyber insurance? Visit our course catalog for more information on our cyber insurance training.