The Cyber Insurance Academy was delighted to host Keely Wilkins and Andy Igel, both from Check Point, in a recent Email Security Masterclass. Topics covered included key trends relating to email security & BEC attacks and the impact of ChatGPT on this attack vector. These Masterclass lecture notes summarize some of the key points raised by our subject matter experts. You can find another summary of some of the other points raised by our speakers here.
Fill in the form to get the Masterclass recording.
Email has become an integral part of our digital existence and permeates our communication in both our personal and professional lives. However, this widespread reliance on email has also exposed a vulnerability, particularly where email is used for business or legal purposes: the email address itself. Often serving as a username for various accounts, including those linked to financial institutions and healthcare portals, these addresses have become low-hanging fruit for malicious cyber threat actors and criminals seeking to exploit unsuspecting users that have access to monetary systems and individuals in positions of authority, making them enticing targets for these bad actors.
Email Security Trends and Terminology: Types of Attack
Phishing, Whaling, Spear Phishing, Zero Click Phishing
While they may seem distinct, they all fall under the broader umbrella of phishing. To understand why we call it “phishing“, envision a fisherman patiently casting his line from the shore or a boat, enticing a fish to take the bait. In essence, this is precisely what bad actors aim to accomplish—they seek to lure unsuspecting users into clicking on a link within an email.
Whaling, on the other hand, is a similar concept but aimed at larger targets, such as C-level executives, board members, or directors. It involves selectively targeting specific individuals or roles, leveraging their position within an organization.
Spear phishing, akin to standing in shallow waters with a spear, involves precisely selecting and targeting an individual based on their role or attributes, rather than just their identity.
As for zero-click phishing, the mere act of opening the email itself can trigger the delivery of malware, requiring no further user interaction.
Pharming
This technique involves harvesting user credentials, encompassing email addresses, usernames, and passwords. The harvested information is then exploited for various purposes, often involving the delivery of malware.
Malware, a combination of “malicious” and “software,” comes in various forms such as spyware, scareware, and adware.
- Spyware invades your privacy, seeking to collect sensitive data or credentials
- Scareware aims to evoke a response by creating a sense of urgency or authority
- Adware is a type of malicious software that secretly installs itself on your device and displays unwanted advertisements and pop-ups.
Business Email Compromise (BEC)
This tactic tricks users into deviating from their normal behaviors, often through urgent requests from a perceived authority figure like a CFO, for example. These attacks are carefully designed to exploit your proximity to financial systems or individuals in positions of power. With email security constantly under siege, it is imperative to stay informed and take proactive measures to protect against these ever-evolving threats.
Email Security Trends: Attacks Executed via Email by Industry
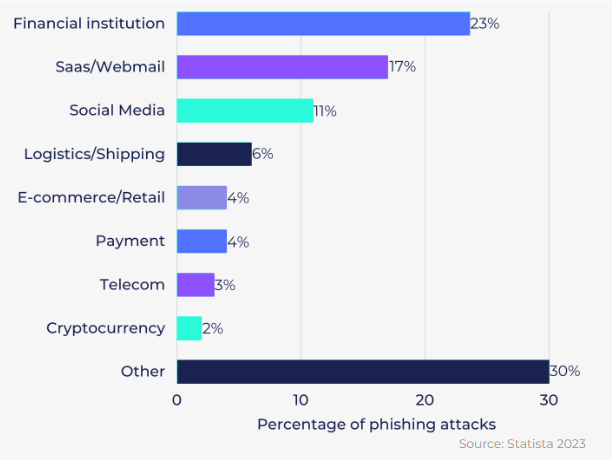
The primary focus of these bad actors lies in gaining access to the user’s financial resources and leveraging their relationships with individuals in positions of authority. Financial institutions, known repositories of wealth, become an obvious target but other valuable targets include Software as a Service (SaaS) providers and webmail platforms. By gaining access to these systems, attackers can exploit sensitive information and disrupt operations. Another avenue exploited by threat actors is social media platforms, which offer a treasure trove of personal data that can be carefully analyzed and utilized to craft sophisticated spear phishing and whaling attacks. Through these carefully orchestrated campaigns, attackers tailor their deceptive tactics to exploit specific individuals or roles, leveraging the wealth of information available on social media platforms.
Top Imitated Brands in Email Attacks
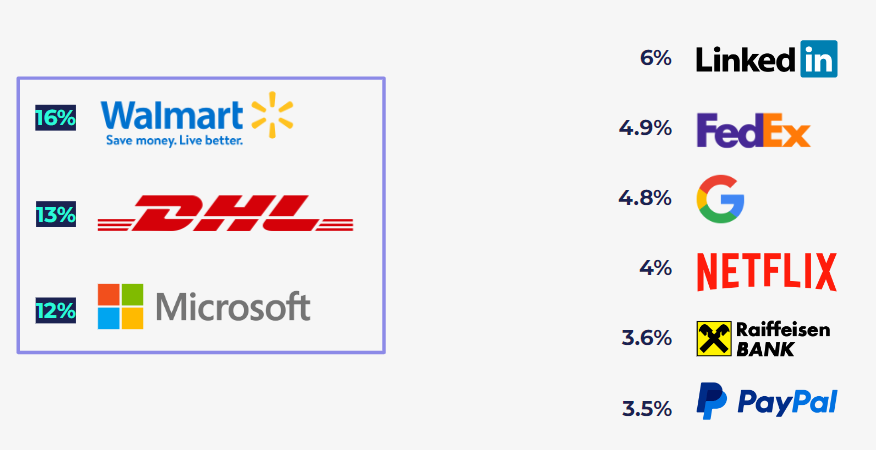
These brands resonate with us on a daily basis, playing integral roles in our routines. Cyber threat actors therefore often exploit the trust and relationships forged between their brands and their customers as a persuasive tool, luring unsuspecting individuals into clicking on malicious links without exercising due caution.
Impact of ChatGPT on Phishing Attacks and Email Security Trends
The media and industry have been engaged in extensive discussions about the capabilities and potential risks of AI, particularly in the context of ChatGPT. As with any powerful tool, its impact can be harnessed for both positive and negative purposes, depending on the intentions of the individual operating it. While ChatGPT holds tremendous promise for the future, its current capabilities are still in the early stages of development.
There have been reports of individuals claiming to have manipulated ChatGPT into writing malware, but these claims remain unsubstantiated and lack conclusive evidence. However, what has been observed is threat actors utilizing ChatGPT to enhance their phishing techniques. ChatGPT’s language skills surpass those of a non-native speaker, enabling threat actors to craft phishing emails that appear more convincing. For instance, if you receive a phishing email with improper grammar or slang, it is easier to identify it as fraudulent. However, with the assistance of AI, these threat actors can refine their language skills, making it increasingly challenging to distinguish between genuine and malicious communications.
Moreover, ChatGPT has the capability to automatically gather personal data from various online sources. Previously, malicious actors had to manually scrape together information from individual accounts. However, with the aid of AI, they can streamline this process, leveraging the technology to extract relevant details more efficiently. By accumulating a wealth of personal information, these perpetrators can then impersonate trusted sources with personalized verbiage, deceiving recipients into clicking on malicious links. This is particularly alarming considering the potential consequences for individuals who possess access to financial systems or hold positions of authority.
In conclusion, in an increasingly email-reliant world, cyber threats exploit vulnerabilities in communication by employing various phishing techniques and leveraging AI-powered tools like ChatGPT to create more convincing and personalized attacks, necessitating heightened cybersecurity measures to protect against these evolving dangers. It is vital that cyber insurance professionals understand these trends and mitigation techniques so that they can better advise their insureds and limit carrier cyber risk exposure.







